This article describes software supply chain attacks and how their mitigation contributes to PCI DSS v4.0 compliance.
PCI DSS v4.0 Requirement 6 and PCI SLC
Mitigation of supply chain attacks contributes to compliance with PCI DSS Requirement 6. When we talk about Requirement 6, it is worth mentioning the PCI Secure Software Lifecycle and PCI Secure Software Standard, which together build the PCI Software Security Framework.
All software that stores, processes, or transmits account data, or that could impact the security of cardholder data and/or sensitive authentication data, is in scope for an entity’s PCI DSS assessment, so the following to the PCI SSF will help you improve the security posture of your software and demonstrate the compliance with the PCI DSS Requirement 6. Additionally, if PCI-listed payment software has been customized, a more in-depth review will be required during the PCI DSS assessment because the software may no longer be representative of the version that was originally validated.
If we look at the PCI DSS requirements from supply chain perspective, we can focus on the following areas:
| Requirement | Comments |
|---|---|
| 6.1 Processes and mechanisms for developing and maintaining secure systems and software are defined and understood. | Affects the approach to the supply chain management process. |
| 6.2 Bespoke and custom software are developed securely. | Mainly touches the in-house software development process, but some aspects of the supply chain management, like the dependencies, can be involved. |
| 6.3 Security vulnerabilities are identified and addressed. | Addresses the supply chain known vulnerabilities mitigation. |
| 6.5 Changes to all system components are managed securely. | Reaches the supply chain changes implementation. |
As it was pointed out before, the PCI SLC requirements are supporting the PCI DSS requirements with the following controls:
Secure Software and Data Management:
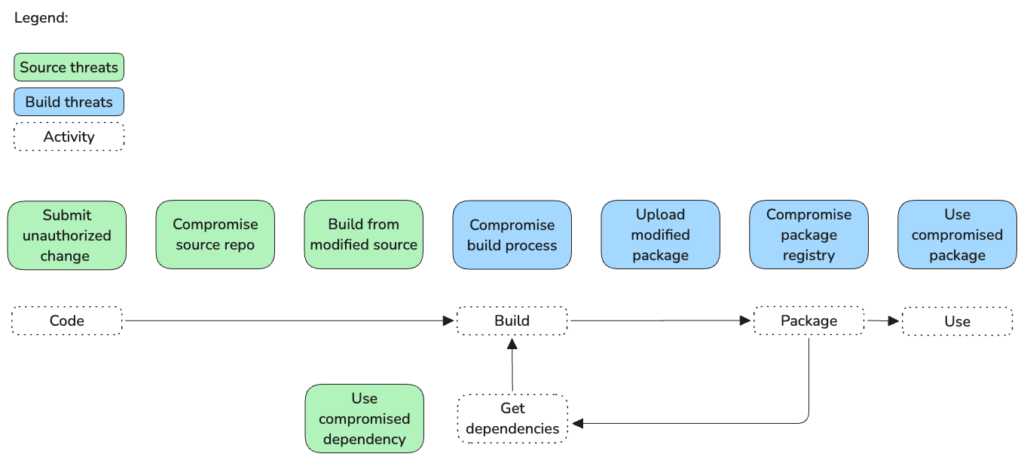
What is a Supply Chain Threat?
Supply chain threat is a malicious activities, targeted towards the supply chain of a product or service. They can come from different directions and have different goals:
How to mitigate Supply Chain Threats?
Note: The main focus of this article is the supply chain threats and their relation to the PCI DSS v4.0 standard. So I will not cover the details of the mitigation techniques here. But this area will be developed in the future articles.
Software Bill of Materials (SBOM)
Strategic adoption of the software bill of materials (SBOMs) as a productive way to maintain compliance and better secure of the software supply chains is becoming more and more popular among the software development organizations.
An SBOM lists all packages and libraries in an application, including all component’s dependencies. This enhanced visibility into what’s in a piece of software makes it easier to identify vulnerabilities and license issues, as well as manage risk from open source components.
CI/CD Process Monitoring
CI/CD process monitoring can be also used to mitigate the supply chain issues. For example, the OpenTelemetry project usage in the context of the CI/CD pipelines monitoring can help identify the supply chain attacks early.
Conclusion
Supply chain protection is an important security practice that helps to improve software security posture. Now, you are aware of how supply chain mitigation contributes to PCI DSS compliance and what requirements are related to supply chain attacks.